Launching a new WordPress website is an exciting milestone — your design is polished, your content is ready, and you finally hit that “Go Live” button. For a brief moment, it feels like your website exists in a perfect digital world. But within hours — sometimes even minutes — you’ll notice something unexpected in your website analytics: a surge of page views from unfamiliar sources.
At first glance, it looks like your site is getting popular fast. But dig a little deeper, and you’ll see the majority of these “visits” aren’t from real users. They’re from bots and hackers scanning for weaknesses. It happens all the time. You have to be prepared for this.
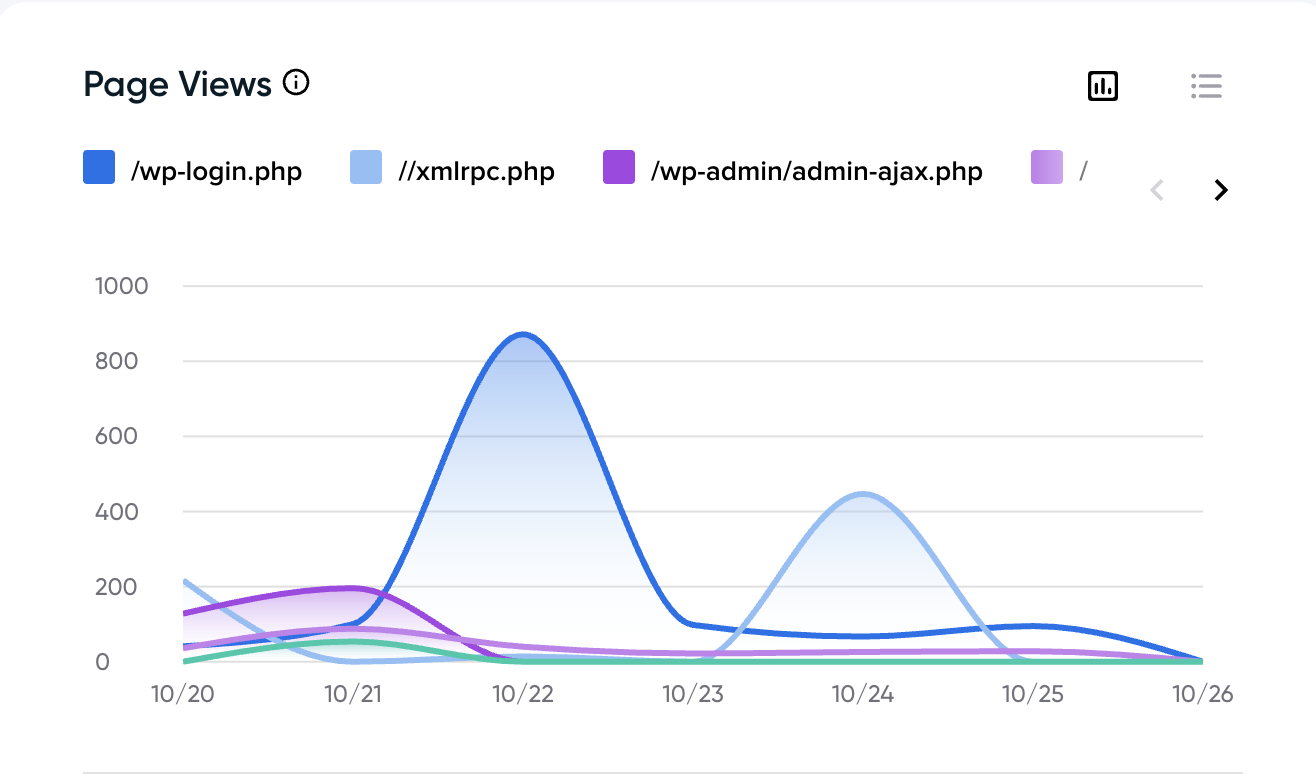
If you check your access logs, you’ll likely see repeated hits to URLs like:
/wp-login.php— attempts to brute-force your WordPress login./xmlrpc.php— an often-abused file that can be used for remote logins and DDoS amplification./wp-admin/admin-ajax.php— a legitimate script frequently targeted for injection or automated attacks.
These aren’t curious visitors. They’re automated scripts scouring the web for vulnerable WordPress installations — hoping to find one that’s been left unprotected.
What You Can Do to Defend Your Site
Securing a WordPress website isn’t a one-time task; it’s an ongoing responsibility. Here are some key measures every site owner should take immediately after launch:
1. Lock down your login page
- Rename or hide
/wp-login.phpusing a plugin like WPS Hide Login. - Limit login attempts to block brute-force attacks.
- Enable two-factor authentication for all admin accounts.
2. Disable or restrict XML-RPC
If you don’t use Jetpack or remote posting tools, disable xmlrpc.php entirely. You can block it via your .htaccess file or a security plugin.
3. Install a reputable security plugin
Tools like Wordfence, iThemes Security, or All-In-One WP Security can detect suspicious behavior, block malicious IPs, and send real-time alerts.
4. Keep everything updated
Themes, plugins, and WordPress core files should always be up-to-date. Many breaches occur because of outdated components.
5. Implement a Web Application Firewall (WAF)
A WAF filters malicious traffic before it reaches your server. Services like Cloudflare or Sucuri add an extra layer of defense against automated attacks.
6. Monitor and respond
Even with strong protections, constant monitoring is essential. Watch your traffic logs for unusual spikes, monitor file integrity, and set up alerts for failed logins.
A new website deserves the same attention and protection as any other business asset. The moment you launch, you become a target — not because hackers know who you are, but because they don’t need to. Their bots will find you automatically.
So before you celebrate your first wave of visitors, make sure you know who’s knocking on your door — and who’s trying to break it down.
The question is: who is monitoring your website analytics?